|
The purpose of this page is to introduce the concepts behind the K2BTools security model.
It also provides a guide for developers wishing to implement security frameworks that should be integrated with objects generated by K2BTools. API Design K2BTools provides a security API with an unique interface. This interface receives a set of “activities” as a parameter. All objects generated by K2BTools patterns and by K2BWebPanelDesigner invoke this API both to control access to the object and to control the visualization of controls in the screen. The API’s interface was designed so that it would be possible to integrate it with any existing security backend.
The idea is that the developer implements this interface in order to achieve one of the following results: Adapt it to its existing security framework. Impement a new security framework. Integrate it to an external tool, for example, the GeneXus Access Manager (GAM).
K2BTools provides a default implementations for the security API, that can be integrated with any application and be modified by the developer as needed.
The implementation, called GAM integration module, integrates with GAM, providing a custom backend with the K2BTools’ look&feel.
In design time, the security to be used by K2BTools is configured in the Transaction Object. To do this K2BTools adds new properties to transactions under the category “K2BTools”.
The properties added are:
- Security: Determines whether security should be checked for the transaction. Is true by default.
- EntitySecurityName: Determines the entity name that should be used. See the full explanation below.
|
Entities handling:
Often in large Knowledge bases, it occurs that many transactions are needed to model a single entity. This can be seen in transactions which are semantically dependant on each other, and provide different views on a single concept.
For example, to model a “Product” entity, it may be required to define many transactions, such as “Product”, “ProductUnit”, or “ProductProvider”.
Using the property “EntitySecurityName”, the developer can establish that those transactions, when invoking the security API, use “Product” as their entity name. This can be useful when implementing the security API’s interface, as all these transactions will be treated the same way by it.
|
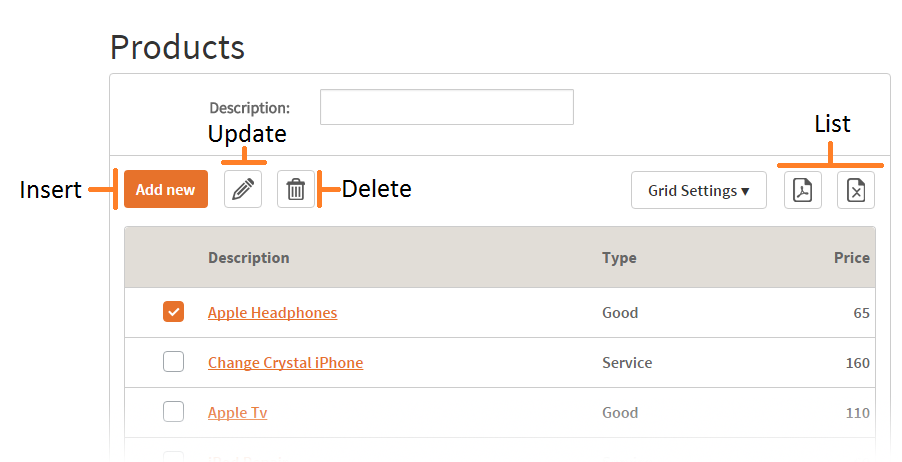
The pattern K2BEntityServices handles access to activities related with operations done on the transactions that define an entity. These activities are:
- Inserting records (Insert)
- Updating records (Update)
- Deleting records (Delete)
- Displaying records (Display)
- Seeing a set of records (of a certain type) as a list (List)
When generating objects, K2BTools patterns check the corresponding permission when opening each object, and disable all controls invoking the object in runtime if needed. This means that if an action is included to access a certain functionality, when generating the action K2BTools include code to verify that the user is allowed to access it, and disables the action if this is not true.
 |
| Standard activity types |
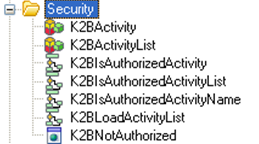
Among K2BTools basic objects, inside the folder User/Security a set of procedures are included, which perform the security checks. Also, a web panel (K2BNotAuthorized) is included. This web panel is displayed to the user when the user tries to access an activity for which it has no permission.
 |
| K2B security basic objects |
All the procedures included invoke the main security procedure, called “K2BIsAuthorizedActivityList”. This is the procedure that the user must implement to integrate security to its system. The default implementation provided by K2BTools always returns true for all activities, that is, allows access to every part of the system to all users.
This procedure receives as a parameter a collection SDT with a set of activities, and returns for each activity a true or false value showing if the activity was authorized or not. The procedure receives a collection parameter on purpose, because there are cases in which the process of determining if a permission should be granted takes time (for example, if a web service needs to be invoked). By checking many permissions at once, part of this processing time can be saved.
 |
 |
| K2BActivitySDT definition |
K2BActivityListSDT definition |
For each activity, the procedure should set if it should be authorized or not, by setting the value of the boolean field “IsAuthorized”
|
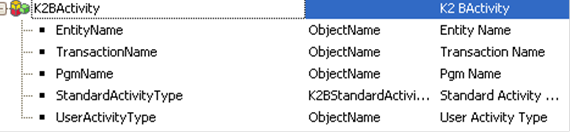
Activity Types:
Activity types can be standard or user defined. Standard activities are the ones handled by patterns (Insert, Delete, Display and List). A domain (K2BStandardActivityType) is included to define these activities.
User defined activity types are independent from standard activity types, and are distinguished by their name. To use an user activity type in K2BActivitySDT, the value of the “StandardActivityType” field must be set to “None” and the name of the activity should be placed in the “UserActivityType” field.
|
As K2BTools know all the activities used in the objects generated by it, a generic procedure called K2BLoadActivityList is generated which returns a set of activities. The output of this procedure can be used by the person implementing the security framework to initialize it with the data from the application.
|